Similar to other chapters, the code for the exercise that follows can be found in the project directory, chapter-9/, inside your Cloud9 IDE. Two subfolders contain the code for both the Python application and the infrastructure for rolling out a DevSecOps CI/CD pipeline. Let’s walk through the contents of both:
- Python Flask application: Thisfolder includes the code required to run a Python-based To-Do list manager application in the form of a Docker container. In addition to the app.py file, a Dockerfile manifest lists all the instructions you will need to create a Docker image.
- DevSecOps CI/CD pipeline constructs: We will be leveraging AWS CDK constructs to deploy the components of our CI/CD pipeline and see what a typical DevSecOps workflow looks like. All the resource constructs we use in the CDK stack are AWS-managed services, so that avoids the need for any foundational infrastructure elements such as VPCs, subnets, internet gateways, and so on.
Before we can commit the code for the Python application and assess it for any security risks, we need to deploy the CDK stack and provision the pipeline components.
Deploying the CDK stack in an AWS account
To deploy the stack resources, we first need to fire thenpm install command so that all the project dependencies can be downloaded. After the installation completes, you can use the cdk synth command to check the CloudFormation template, if you like.
At this point, we are all set to deploy the stack in the AWS account, which will set up all the stages and corresponding actions of the pipeline using the AWS CodePipeline service: aws-devops-simplified:~/environment/chapter-9/devsecops-cicd-pipeline $ cdk deploy……
✨Synthesis time: 12.65sDeliveryPipelineStack: start: Building46e40c3e0f5b985e8b4b1bbc5c4eb-24cacee4d46e40c3e0f5b985e8b4b1bbc5c4eb24cacee4d04d15ecbcbecbc4839d8f-9d1cf:current_account-current_region…Do you wish to deploy these changes (y/n)? yFDeliveryPipelineStack: deploying… [1/1]…DeliveryPipelineStack: creating CloudFormation changeset…
✅DeliveryPipelineStack ✨Deployment time: 202.82s
After the CDK application has been successfully deployed, you can access the CodePipeline service to see all the stages and corresponding actions that have been provisioned. You will see something similar to Figure 9.3:
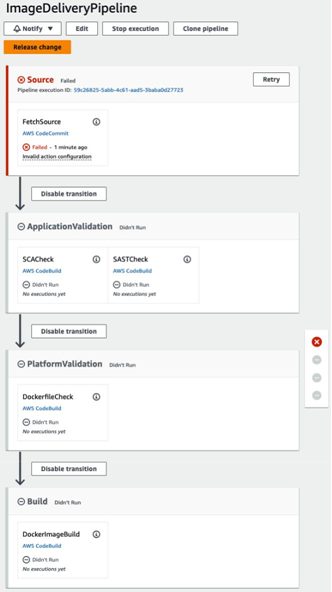
Figure 9.3 – Different stages of the CI/CD pipeline
As you can notice, the first stage reports a failure, which is expected since there is no code in the freshly provisioned CodeCommit repository. So, let’s go ahead and commit the application code into the repository. CodeCommit recommends using the git-remote-codecommit plugin for authenticating against the HTTPS (GRC) endpoint. This GRC endpoint can be retrieved from the CodeCommit service page for your repository, in the AWS web console. The git-remote-codecommit plugin is already included in the Cloud9 IDE that you’ve installed in your AWS account.
One last step before we can see the pipeline in execution is to initialize a local git repository and set up the git remote so that it points to our CodeCommit repository in the AWS account. We just need to push the application code, so let’s switch the working directory as well: aws-devops-simplified:~/environment/chapter-9 $ cd chapter-9-flask-app/aws-devops-simplified:~/environment/chapter-9/chapter-9-flask-app $ git init .aws-devops-simplified:~/environment/chapter-9/chapter-9-flask-app $ git checkout -b masteraws-devops-simplified:~/environment/chapter-9/chapter-9-flask-app $ git add .aws-devops-simplified:~/environment/chapter-9/chapter-9-flask-app $ git commit -m “Sample application for DevSecOps pipeline”
After files have been added to Git’s staging area, we can push them to the CodeCommit repository: aws-devops-simplified:~/environment/chapter-9/chapter-9-flask-app $ git remote add origin codecommit::eu-central-1://image-delivery-pipelineaws-devops-simplified:~/environment/chapter-9/chapter-9-flask-app $ git push origin master…
As soon as the commits are registered in CodeCommit, the pipeline execution begins. CodePipeline can now source the code from the CodeCommit repository on the configured branch (master). Let’s dive into the result of security assessments that are configured in the pipeline.
