Therefore, my advice for companies who are just getting started with their AWS foundation would be to leverage the service for what it offers, and let it play its role in the bigger Landing Zone arena. You will need a complementing solution or framework to implement other functionalities that are not bundled as part of the service. For companies that have an existing Landing Zone, or framework that works with IaC, I see less value in switching over to Control Tower. The latter is more specific to companies that are comfortable getting hands-on and maintaining such solutions at scale on their own. Due to the variety of implementation options here, it’s out of this chapter’s scope to cover all possible implementation scenarios. In the following sections, we will focus more on using Control Tower alongside another framework of your choice to build an end-to-end Landing Zone platform.
Before we get to the topic of integrating a deployment solution or framework, let’s ensure we have a good understanding of the Control Tower service by looking at a diagram:
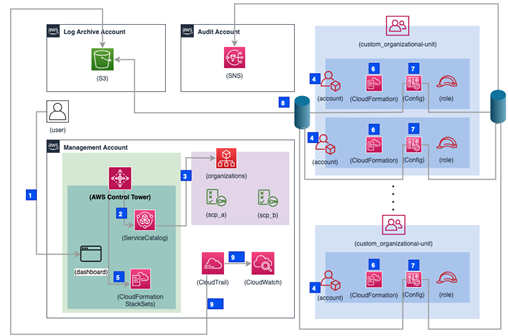
Figure 11.3 – Orchestration of different AWS services by AWS Control Tower
This diagram is not an extensive representationof every single function that AWS Control Tower takes care of under the hood. Rather, it aims to highlight the different steps involved in an account creation workflow, followed by deploying resources into it. Let’s take a look at this diagram in more detail:
- The platform developer uses the AWS Control Tower console UI to register a new account creation request, as well as the target OU the account should be part of.
- AWS Control Tower passes on the request to Account Factory (a Service Catalog product), which initiates the account provisioning workflow.
- Under the hood, the request results in the AWS Organizations API being invoked to create a new account.
- An AWS account gets created and placed in the target OU, which defines what kind of policy controls and governance will apply to the workloads hosted in this account.
- AWS CloudFormation StackSets, a service feature that automatically deploys stacks into an account-region combination, already has some reusable templates defined by the AWS Control Tower service. A new stack instance for the StackSet definition is created by AWS Control Tower, which initiates the provisioning of an AWS CloudFormation template in the target account, in the respective region. As an example, if you are governing three regions in the target account, you get three stack instances.
- AWS CloudFormation stack provisioning starts inside the target account, in a particular AWS region, and deploys resources such as the AWS Config recorder, IAM roles, and other things that are needed to manage this account in a compliant manner.
- AWS Config sets up a recorder that monitors changes to all resources in the accounts and sets up a delivery channel
- The configuration recorder is a mechanism that registers any resource configuration changes and sends the data to a centralized S3 bucket for auditing needs; notifications are sent to an SNS topic in parallel. The SNS notifications are aggregated per region and can be used for advanced analysis and automated alerts by the security teams when unexpected resource changes happen.
- When you first install AWS Control Tower, it creates an organization-wide AWS CloudTrail trail that automatically picks up new accounts in the organization and aggregates trail data into the central S3 bucket in the LogArchive account. It also pushes logs to the CloudWatch log group in the management account. This provides audit and investigation possibilities to a central security team without the need to access all the accounts in the Landing Zone.
All of these features are available out of the box with Control Tower, which takes roughly 1 hour to install. As you might have noticed, there is no application or organization-specific deployment need that the service covers. So far, it’s a prescriptive setup of good practices that will be rolled out as soon as an account is created. To roll out other AWS services and resources, you would need a deployment solution or framework that fills the gaps needed to get to a complete Landing Zone platform.
Next, let’s have a look at CfCT. This is an AWS-supported solutionthat integrates with the AWS Control Tower service to roll out custom resources defined by AWS CloudFormation templates. Say you require a particular IAM role for your security scanning third-party platform that should be automatically deployed in all AWS accounts as soon as they are provisioned. CfCT can help with this. Alternatively, you might want to deploy certain Config rules into all AWS accounts contained in the production OU, but not others.
